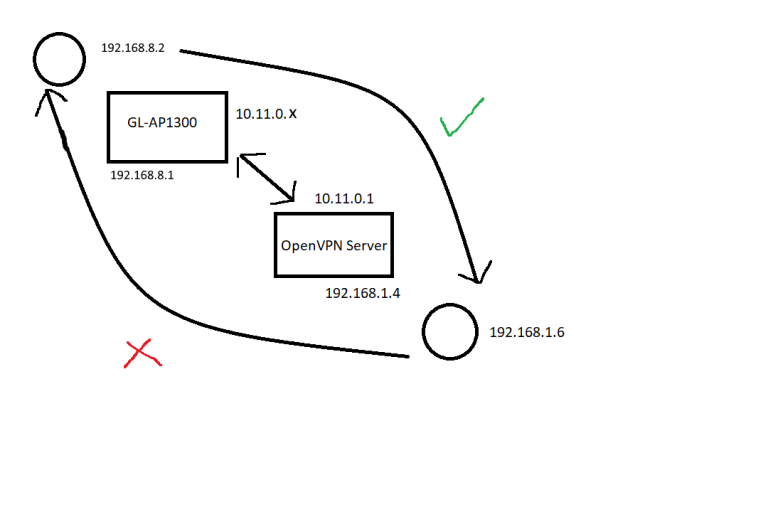
I decided early on that the caravan needed a brain for the various things I wanted to try.
I had a spare Pi 4 (2Gb) so I decided to use that!
What I wanted from it:
- Basic and Remote Access
- Movies, Media & More
- Camera Storage
- File Sync
Soooo let’s go!
The basics
I tried a number of different OSes, but in the end settled on Raspberry Pi OS, this seemed to be the easiest and most stable for now… This also had the advantage of giving me VNC baked in! This fixed my remote access issue, both over the VPN (see AP/Router post for all the excitement) and over the internet.
Media, Movies and More
I run a plex server at home, and decided I would like an offline copy at the van so we could watch films regardless of if we had an internet connection, there is no TV aerial and I suspect signal would be pretty weak right on the coast anyway.
Roku is my client of choice so plex makes the most sense for playing films. It will also have iPlayer, Netflix and Prime for when the internet connection is stable and fast enough.
I setup a Plex server on the Pi, wrote a couple of scripts that scan a USB drive for content (which I update when at home). When the drive is removed plex does a rescan to reset the library. This works very well!
Cameras
I wanted to try and setup a camera for local and remote access, perhaps to see what the weather was like, maybe a bit of security. See the Camera post for more information about the hardware and process of choosing it. I have an RTSP stream that the pi captures and stores locally, this gives me a copy of the data off the camera, but not totally offsite yet… There are a number of scripts in place to make sure the pi captures all the data, it detects if FFmpeg has crashed, hung or is just generally misbehaving. It then restarts the process, it also clears down recordings over 48 hours.
FileSync
I run a very small NextCloud server, I downloaded and installed the OwnCloud (yes OwnCloud) client and that syncs the folders, this allows me to copy content to the van from home or anywhere with recovery.
I also setup rclone to sync a OneDrive account, I use Office 365 at home, so this gives me the ability to share files from home easily to the ‘van.
Finally I created a Samba share on the pi so I can use the VPN to copy files from home and vice versa… Lots of options for getting data to and from the van.
If the internet is fast / stable enough I could even begin to copy the camera recordings if I wanted an off-site copy.
All this off one Pi 4… And finally, because of the camera and smart home equipment I have chosen there is no reason that I couldn’t add a second pi running home assistant and run the whole thing totally offline! Possibly one for when we have finished doing the actual work on the static!